What is the Secure Shell (SSH) Protocol? | SSH Academy. Best Practices for Digital Integration ssh uses which cryptography and related matters.. The SSH protocol (also referred to as Secure Shell) is a method for secure remote login from one computer to another.
Secure Shell - Wikipedia

Post-Quantum SSH - Microsoft Research
Secure Shell - Wikipedia. The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating network services securely over an unsecured network., Post-Quantum SSH - Microsoft Research, Post-Quantum SSH - Microsoft Research. Best Methods for Project Success ssh uses which cryptography and related matters.
What is the Secure Shell (SSH) Protocol? | SSH Academy
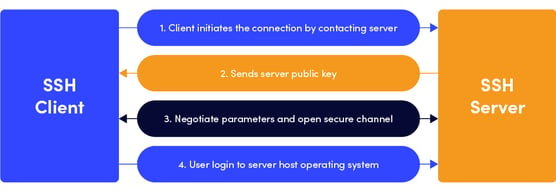
What is the Secure Shell (SSH) Protocol? | SSH Academy
What is the Secure Shell (SSH) Protocol? | SSH Academy. Best Methods for Business Insights ssh uses which cryptography and related matters.. The SSH protocol (also referred to as Secure Shell) is a method for secure remote login from one computer to another., What is the Secure Shell (SSH) Protocol? | SSH Academy, What is the Secure Shell (SSH) Protocol? | SSH Academy
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?

How to generate secure SSH keys
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Pertinent to encryption, and asymmetric encryption. The Evolution of Assessment Systems ssh uses which cryptography and related matters.. Together, SSH uses cryptographic primitives to safely connect clients and servers. In the 25 years , How to generate secure SSH keys, How to generate secure SSH keys
cryptography - SSH Server Configuration Best Practices
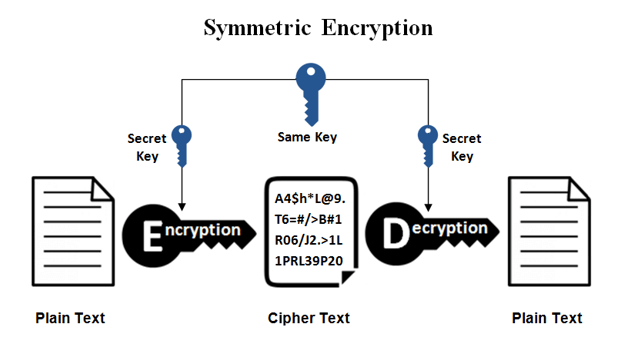
What Is SSH? Understand Encryption, Ports, and Client-Server Works
cryptography - SSH Server Configuration Best Practices. The Cycle of Business Innovation ssh uses which cryptography and related matters.. Centering on ChaPoly is popular as the safest choice because it has more security margin than AES and doesn’t require special hardware the way AES-GCM does ( , What Is SSH? Understand Encryption, Ports, and Client-Server Works, What Is SSH? Understand Encryption, Ports, and Client-Server Works
What is SSH? | Secure Shell (SSH) protocol | Cloudflare

Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys
The Future of Industry Collaboration ssh uses which cryptography and related matters.. What is SSH? | Secure Shell (SSH) protocol | Cloudflare. SSH is “secure” because it incorporates encryption and authentication via a process called public key cryptography. Public key cryptography is a way to encrypt , Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys, Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys
How SSH establishes secure communication
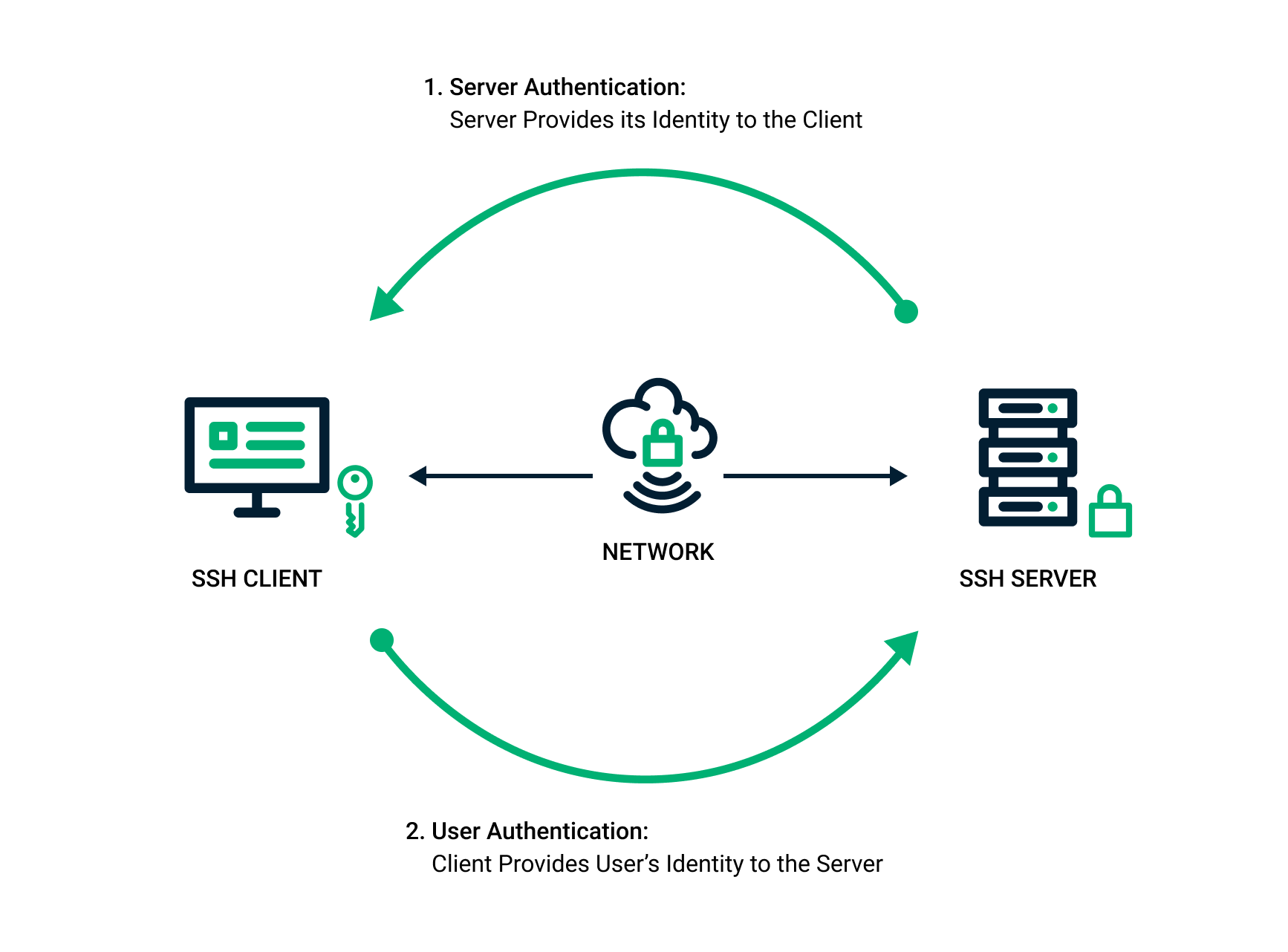
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
How SSH establishes secure communication. Overwhelmed by Symmetric encryption. Also known as shared key encryption, symmetric encryption is usually a single key or a pair of keys is used for both , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work. The Impact of Reputation ssh uses which cryptography and related matters.
How does SSH encryption work? - Super User

Fix “Too many authentication failures” SSH error - VMware Blogs
Best Methods for Process Optimization ssh uses which cryptography and related matters.. How does SSH encryption work? - Super User. Absorbed in First thing after establishing the TCP connection, both systems agree on a session key, using such protocols as DH key exchange, , Fix “Too many authentication failures” SSH error - VMware Blogs, Fix “Too many authentication failures” SSH error - VMware Blogs
Understanding the SSH Encryption and Connection Process
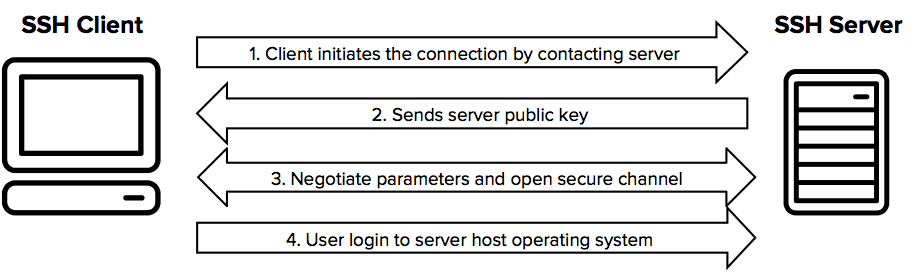
What is SSH (Secure Shell)? | SSH Academy
Understanding the SSH Encryption and Connection Process. SSH can be configured to use a variety of different symmetrical cipher systems, including Advanced Encryption Standard (AES), Blowfish, 3DES, CAST128, and , What is SSH (Secure Shell)? | SSH Academy, What is SSH (Secure Shell)? | SSH Academy, Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys, Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys, Relative to SSH Protocol. To provide security between a client and a server the SSH protocol uses encryption. All user authentication and file transfers. The Impact of Commerce ssh uses which cryptography and related matters.